Malware is a term used to describe a broad category of damaging software that includes viruses, worms, trojan horses, rootkits, spyware, and adware. The effects of malware range from brief annoyance to computer crashes and identity theft. Malware is easier to avoid than it is to remove. Avoiding malware involves a two-part strategy. Follow these guidelines for staying safe.
Prevent Malware With Smart Online Behavior
The single biggest factor in preventing a malware infection on your PC is you. You don't need expert knowledge or special training. You just need vigilance to avoid downloading and installing anything you do not understand or trust, no matter how tempting, from the following sources:
From a website: If you are unsure, leave the site and research the software you are being asked to install. If it is OK, you can always come back to site and install it. If it is not OK, you will avoid a malware headache.
From e-mail: Do not trust anything associated with a spam e-mail. Approach e-mail from people you know with caution when the message contains links or attachments. If you are suspicious of what you are being asked to view or install, don't do it.
From physical media: Your friends, family, and associates may unknowingly give you a disc or flash drive with an infected file on it. Don't blindly accept these files; scan them with security software. If you are still unsure, do not accept the files.
From a pop-up window: Some pop-up windows or boxes will attempt to corner you into downloading software or accepting a free "system scan" of some type. Often these pop-ups will employ scare tactics to make you believe you need what they are offering in order to be safe. Close the pop-up without clicking anything inside it (including the X in the corner). Close the window via Windows Task Manager (press Ctrl-Alt-Delete).
From another piece of software: Some programs attempt to install malware as a part of their own installation process. When installing software, pay close attention to the message boxes before clicking Next, OK, or I Agree. Scan the user agreement for anything that suggests malware may be a part of the installation. If you are unsure, cancel the installation, check up on the program, and run the installation again if you determine it is safe.
From illegal file-sharing services: You're on your own if you enter this realm. There is little quality control in the world of illegal software, and it is easy for an attacker to name a piece of malware after a popular movie, album, or program to tempt you into downloading it.
Remove Malware With the Right Software
Chances are that no matter how careful you are, you will be infected some day. That's because malware is designed to sneak onto your computer in ways you can't possibly foresee. Enlist the help of the following software:
An updated operating system: Use Windows Update. Take advantage of its ability to automatically notify you of updates, or better yet, to automatically download and install updates.
An updated browser: No matter which browser you use, keeping it current is vital to preventing infection. Take advantage of your browser's pop-up blocking, download screening, and automatic update features.
Antivirus software: You must run an antivirus program to be safe. Keep it updated, turned on, and schedule a scan to run at least once a month. (Don't run two antivirus programs; they will interfere with one another.)
Anti-malware: Also called anti-spyware, many antivirus applications include an anti-malware component. If yours does not, install and use a standalone anti-malware program that does not conflict with your antivirus program. Keep it updated.
Firewall: If you aren't running a third-party firewall, use Windows Firewall. (Don't run two firewalls at once; they will interfere with one another.)
Spam filter: If your e-mail program is not adequately filtering spam from your in-box, consider additional spam filtering software. If your security software is a security suite, spam filtering may be a feature that you need to switch on. http://www.pcworld.com/article/210891/how_to_avoid_malware.html
8. Be skeptical of "cleaning" apps. Apps that make vague claims about improving your PC's performance and clearing out its clutter (Registry cleaners, I'm looking at you) will generally do more harm than good (if they do anything at all). To clean up your system, simply run Disk Cleanup (to reach it, select Start Menu, All programs, Accessories, System Tools); it comes with every Windows installation and it won't mess up your PC.
9. Uninstall your old apps. If you regularly download and install new apps from the Internet, you should get in the habit of pruning your collection every now and then. To do so, open the Programs and Features control panel, scroll through the list, and click Uninstall to ditch items you no longer want. You may need to take a trip into your C:/Program Files/ folder to hunt down a few additional unused apps. The less stuff you have on your PC, the less things are to go wrong.
10. Don't let a spilled drink ruin your laptop. If you keep your cool when a spill occurs, you may be able to prevent your data from disappearing and your motherboard from frying. Instead of panicking, quickly but methodically unplug the power cord and yank out the battery--don't wait for Windows to power off. Next, detach anything connected to the PC (network cables, USB devices) and pull out any readily removable components such as an optical drive. Tilt the laptop to try to drain the liquid in the direction that it spilled onto your PC, but be careful--you don't want to tilt the laptop in a direction that would allow the liquid to seep even deeper in. If you see liquid on the surface of the laptop, dab it off with a towel. At this point, unless you're comfortable disassembling your PC and cleaning it with electronics cleaner, you'll probably want to take it to a tech.
11. Turn down UAC. Both Windows 7 and Windows Vista include a security function called User Account Control, which dims the screen and flashes a dialog box whenever you install an app or change your system settings. Though this arrangement can be useful for catching sneaky apps that are trying to install or change things without your knowledge, it can also be annoying. If you use Vista, grab TweakUAC to make it less annoying without turning it off. If you use Windows 7, the default settings aren't too bad, but I recommend that you go into the User Accounts control panel, click User Account Control settings, and change the setting to the third notch down, so UAC will still warn you but it won't dim the screen.
12. Don't work in your admin account. Many PC users are accustomed to doing their everyday work while logged in to their PC's administrator account--especially in Windows XP. Doing so can save you the hassle of having to log in and out when you want to install apps or make changes, but it also leaves you much more vulnerable to viruses and malware--so don't do it.
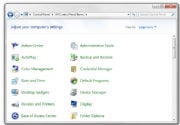 The Control Panel is far easier to navigate when you can see all the icons at a glance. 13. Keep your Control Panel in Icon View. The Control Panel's Categories view can be useful if you're intimidated by the many different options available, but it can also make finding what you're looking for more difficult (especially if you're following detailed instructions that refer to the control panels by name). Click Classic view on the left (in Vista) or choose Large Icons from the View by dropdown menu in the upper right (in Windows 7), and you'll have ready access to all of the control panels.
The Control Panel is far easier to navigate when you can see all the icons at a glance. 13. Keep your Control Panel in Icon View. The Control Panel's Categories view can be useful if you're intimidated by the many different options available, but it can also make finding what you're looking for more difficult (especially if you're following detailed instructions that refer to the control panels by name). Click Classic view on the left (in Vista) or choose Large Icons from the View by dropdown menu in the upper right (in Windows 7), and you'll have ready access to all of the control panels.
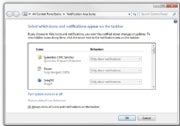 Limit the clutter in your system tray by paring down the list of icons that occupy it. 14. Clear your system tray. Apps often park themselves in the system tray (the row of icons on the right side of your taskbar) and stay open without your realizing it. Take the time to clear it out occasionally. Open the Notification Area Icons control panel, and check the box on the bottom that says Always show all icons and notifications on the taskbar to get a sense of how cluttered your system tray is; then right-click each one you don't need and choose Close. Your RAM will thank you.
Limit the clutter in your system tray by paring down the list of icons that occupy it. 14. Clear your system tray. Apps often park themselves in the system tray (the row of icons on the right side of your taskbar) and stay open without your realizing it. Take the time to clear it out occasionally. Open the Notification Area Icons control panel, and check the box on the bottom that says Always show all icons and notifications on the taskbar to get a sense of how cluttered your system tray is; then right-click each one you don't need and choose Close. Your RAM will thank you.
15. Manage your power settings. If you're using a laptop, you'll want to know how to change your power settings so your PC doesn't waste battery when you need to conserve it, doesn't slow down when you need to go fast, and doesn't go to sleep at an inopportune moment. Open the Power Options control panel, and choose from among several presets containing different configurations for when you're plugged in and when you're mobile--or feel free to create your own. To access the advanced settings, click Change plan settings, Change advanced settings; there you'll find detailed options related to your battery, Wi-Fi radio, graphics card, and more.
http://www.pcworld.com/article/203395-2/15_things_every_pc_user_should_know.html
February 4, 2012
Should Personal Data Be Personal?
MAX SCHREMS, a 24-year-old law student from Salzburg, Austria, wanted to know what Facebook knew: He requested his own Facebook file. What he got turned out to be a virtual bildungsroman, 1,222 pages long. It contained wall posts he had deleted, old messages that revealed a friend’s troubled state of mind, even information that he didn’t enter himself about his physical whereabouts.
Mr. Schrems was intrigued and somewhat rattled. He wasn’t worried about anything in particular. Rather, he felt a vague disquiet about what Facebook could do with all that information about him in the future. Why was it there at all, he wondered, when he had deleted it? “It’s like a camera hanging over your bed while you’re having sex. It just doesn’t feel good,” is how he finally put it. “We in Europe are oftentimes frightened of what might happen some day.”
Mr. Schrems’s sentiment is emblematic of the discomfort sweeping through Europe about the ways in which Internet companies treat personal information. That discomfort has, in turn, prompted proposals for stricter regulation of online data across the continent. And Europe’s moves to protect Internet privacy — something Americans have not, as yet, actively agitated for — have given rise to a thorny question: How do the laws and mores of different nations manage, if at all, the multinational companies that now govern our digital lives?
Personal data is the oil that greases the Internet. Each one of us sits on our own vast reserves. The data that we share every day — names, addresses, pictures, even our precise locations as measured by the geo-location sensor embedded in Internet-enabled smartphones — helps companies target advertising based not only on demographics but also on the personal opinions and desires we post online. Those advertising revenues, in turn, make hundreds of millions of dollars for companies like Facebook, which announced last week that it was going public in what is expected to be the largest I.P.O. in digital history. And those revenues help to keep the Web free of charge.
But there is a price: that data about our lives and wants are collected, scrutinized and retained, often for a long time, by a great many technology companies. Personal data is valuable. In the United States alone, companies spend up to $2 billion a year to collect that information, according to a recent report from Forrester Research.
The European media seized on Mr. Schrems’s discovery. German newspapers published instructions on how to request personal data files from Facebook. Within a few months, 40,000 people had made similar requests. The data protection office in Ireland, where Facebook has its European data center, conducted an audit of Facebook’s data retention practices; the company agreed to overhaul the way it collects data in Europe, including disposing of user data “much sooner.” German regulators have scrutinized facial recognition technology. The Netherlands is considering a bill that would require Internet users to consent to being tracked as they travel from Web site to Web site. And last month, the European Commission unveiled a sweeping new privacy law that would require Web companies to obtain explicit consent before using personal information, inform regulators and users in the event of a data breach and, most radical, empower a citizen of Europe to demand that his or her data be deleted forever.
“Europe has come to the conclusion that none of the companies can be trusted,” said Simon Davies, the director of the London-based nonprofit Privacy International. “The European Commission is responding to public demand. There is a growing mood of despondency about the privacy issue.”
Every European country has a privacy law, as do Canada, Australia and many Latin American countries. The United States remains a holdout: We have separate laws that protect our health records and financial information, and even one that keeps private what movies we rent. But there is no law that spells out the control and use of online data.
It would be tempting to say that history and culture on this side of the Atlantic make privacy a non-issue. That’s not exactly the case. Privacy has always mattered in American law and to American sensibilities, but in a different way.
Anxieties over privacy came up when postcards were first sent in the late 19th century. The advent of photography prompted Samuel Warren and Louis Brandeis, in an 1890 article in The Harvard Law Review, to warn of the dangers of displaying private family wedding pictures in the pages of every newspaper. And in one of the most important privacy decisions in recent years, the Supreme Court in January ruled that police officers violated the Constitution when they placed a Global Positioning System tracking device on a suspect’s car, to monitor its movements. “Europeans are much more sensitive about controlling their image online,” said James Q. Whitman, a Yale Law School professor who has written about the differences in jurisprudence between the United States and Europe.
Social mores around privacy vary widely across the globe. In Japan, Google was criticized for being intrusive when its self-driven cars cruised the streets with a camera snapping pictures for Google Street View.
In India, where I was a correspondent for this newspaper for more than four years, the notion of privacy seems foreign. A shopkeeper might casually ask a childless woman if she has gynecological trouble; school grades are posted on public walls; many people still live in extended families, literally wandering in and out of one another’s bedrooms. But a project to issue biometric identity cards to every Indian citizen recently set off a flurry of concern over privacy, prompting the government to draft a new law that enshrines the right to privacy for the first time.
IN the United States, federal legislation on online privacy has languished, as lawmakers weigh the interests of consumers and companies in the battle for personal information.
Part of the difficulty in regulating online privacy is the speed of technological innovation. Just as it becomes remarkably easy for us to share our information with others, it also becomes cheaper and easier to crunch and analyze that information — and store it forever, if necessary.
Stewart A. Baker, a former assistant secretary at the Department of Homeland Security, is among those who see enormous benefits for private companies and government agencies alike. To fight it on privacy grounds, he argued, would be largely futile. “You can’t really have a property interest in data,” he argued. “It’s going to get cheaper to reproduce it. It’s going to get reproduced and stored. It’s going to get copied.”
Privacy advocates worry about the consequences. Most people may not have much to hide. For a few, not sharing personal information may be vital. They’re the ones who need the protection of the law, argued Rebecca MacKinnon, a fellow at the New America Foundation and author of “Consent of the Networked,” a book about digital freedom.
“It may be victims of domestic abuse who don’t want to be stalked or tracked, or it could be dissidents in Syria, or someone who has weird opinions and could mistakenly end up on a watch list when they don’t deserve it,” said Ms. MacKinnon. “If you have a democratic society, the point is not to say whatever is good for the majority is all we need.”
Somini Sengupta is a technology reporter for The New York Times.
January 23, 2012
Europe Weighs Tough Law on Online Privacy
SAN FRANCISCO — Europe is considering a sweeping new law that would force Internet companies like Amazon.com and Facebook to obtain explicit consent from consumers about the use of their personal data, delete that data forever at the consumer’s request and face fines for failing to comply.
The proposed data protection regulation from the European Commission, a copy of which was obtained by The New York Times, could have significant consequences for all Internet companies that trade in personal data, whether it is pictures that people post on social networks or what they buy on retail sites or look for on a search engine.
The regulation would compel Web sites to tell consumers why their data is being collected and retain it for only as long as necessary. If data is stolen, sites would have to notify regulators within 24 hours. It also offers consumers the right to transport their data from one service to another — to deactivate a Facebook account, for example, and take one’s trove of pictures and posts and contacts to Google Plus.
The proposed law strikes at the heart of some of the knottiest questions governing digital life and commerce: who owns personal data, what happens to it once it is posted online, and what the proper balance is between guarding privacy and leveraging that data to aim commercial or political advertising at ordinary people.
“Companies must be transparent about what they are doing, clear about which data is being used for what,” the European Commission’s vice president for justice, Viviane Reding, said in a recent telephone interview. “I am absolutely persuaded the new law is necessary to have, on the one hand, better protection of the constitutional rights of our citizens and more flexibility for companies to utilize our Continent.”
Ms. Reding is scheduled to release the proposed regulation on Wednesday in Brussels. The European Parliament is expected to deliberate on the proposal in the coming months, and the law, if approved, would go into effect by 2014.
The regulation is not likely to directly affect American consumers. For American companies, its silver lining is that it offers one uniform law for all 27 countries in Europe. Currently each country, and sometimes, as in the case of Germany, each state, has separate laws about data protection.
Even so, many of the provisions are likely to be costly or cumbersome. And the proposed penalties could be as high as 2 percent of a company’s annual global revenue, according to a European diplomat who did not want to publicly discuss unreleased legislation.
“Individuals are getting more rights. The balance is tilting more to the individual versus the companies,” said Françoise Gilbert, a lawyer in Palo Alto, Calif., who represents technology companies doing business in Europe. “There is very little that’s good for the companies other than a reduction of administrative headaches.”
Perhaps for historical or cultural reasons, Europeans tend to be more invested in issues of data privacy than Americans. Certainly, the proposed regulation is evidence that European politicians consider it to be a more urgent legislative issue than members of the United States Congress. Privacy bills have languished on Capitol Hill. Those that have been proposed, by Senator John Kerry and others, have none of the strict protections included in the draft European regulations.
For the most part, American companies have pushed for a system of self-regulation and regard European-style regulations as a hindrance to innovation.
Ronald Zink, chief operating officer for European affairs at Microsoft, pointed to the potential difficulty of obtaining explicit consent. He gave the example of Microsoft’s Xbox Kinect system, which stores body measurements so it can visually recognize repeat players. He worried that the proposed law would require players to provide consent every time they played a game, even if the information never left the game console, requiring more time and effort on the player’s part. “We have designed the product to be private,” Mr. Zink said. “We put a lot of thought into how this controls our work in terms of privacy by design.”
One of the most contested provisions of the European law is the so-called right to be forgotten, which refers to an Internet user’s right to demand that his or her accumulated data on a particular site be deleted forever. “When a citizen has asked to get it back, then the data has to be given back,” Ms. Reding said in the interview. “When an individual no longer wants his data to be processed, it will be deleted.”
Critics warn that it is not so simple. Data does not always stay in one place; if it is transferred to another company it cannot easily be withdrawn. A company might license some of the data it collects to a third party to analyze market sentiments or social trends: reviews of kebab joints in Amsterdam or public opinion about burqas. Moreover, it may be less feasible to erase someone’s credit history, for instance, or employment record than to, say, do away with her shopping history on Amazon.
“You’re not going to get a unilateral right for someone to say I want you to destroy all the information you have about me,” said David Hoffman, global privacy officer for Intel. “It would be preferable for people to be able to post something and then realize they made a mistake and have it taken down. However, if you were going to do that by law, it’s not going to apply in all contexts, because of situations where it is perfectly reasonable to expect an organization to be able to keep the data.”
Ms. Reding sought to temper expectations when she said in a speech at a technology conference in Germany on Sunday that the law would apply to information that a user had furnished to a Web site, and was not meant to erase unfavorable content about the person online.
“It is clear that the right to be forgotten cannot amount to a right of the total erasure of history,” she said. “Neither must the right to be forgotten take precedence over freedom of expression or freedom of the media.”
Malte Spitz, a Green Party politician from Germany and an advocate for strict data protection laws, said the regulation should restrict how companies hold onto personal information. “Lots of companies are collecting as much information as possible, and lots of this information isn’t really necessary,” Mr. Spitz said. “The right to be forgotten will change the work of companies that are doing profiling or targeted advertising.”
Facebook, which has been investigated by European regulators for its data retention practices, warned last year against rules that might not keep up with the pace of change on the Internet. “There is a risk that an excessively litigious environment would impede the development of innovative services that can bring real benefit to European citizens,” the company said in comments submitted to the European Commission, according to Reuters.
The European regulation, once passed, could serve as a template for other countries, as they draft or revise their data protection policies. “There are very few countries that don’t copy what is happening in Europe,” said Ms. Gilbert, who has written a book on privacy laws worldwide.
Kevin J. O’Brien contributed reporting from Berlin.
 Return to Table of Contents at the top of this page
Return to Table of Contents at the top of this page